In today’s fast-paced digital world, maintaining robust security isn’t just a good idea; it’s an absolute necessity. Organizations of all sizes face a constant barrage of threats, from phishing attempts and malware to insider risks and accidental data breaches. Keeping a vigilant eye on every corner of your operations can feel overwhelming, especially when you’re trying to balance daily tasks with an ever-present need for security oversight. This is where structured security practices become your best friend, helping you transform chaotic monitoring into an organized, proactive defense strategy.
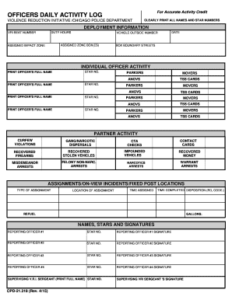
One of the most effective yet often overlooked tools in a comprehensive security arsenal is the humble activity log. It serves as a meticulous record of events, a chronological narrative of what happens within your systems and by your personnel. But creating and maintaining such a log from scratch can be a daunting task, riddled with inconsistencies and potential omissions. This is precisely why a well-designed security daily activity log template can be a game-changer, providing a standardized framework that ensures nothing important slips through the cracks.
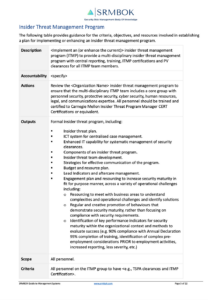
Why a Security Daily Activity Log Template is Indispensable for Your Organization
Implementing a security daily activity log template offers a multitude of benefits that extend far beyond simple record-keeping. At its core, it establishes a consistent method for documenting security-related events, which is crucial for maintaining an auditable trail and fostering a culture of accountability. Imagine needing to trace back a suspicious network activity or an unauthorized file access; without a clear, systematic log, you’d be searching in the dark. This template provides that much-needed light, illuminating the sequence of events and the roles played by various systems and individuals.
Moreover, a comprehensive log acts as a cornerstone for regulatory compliance. Industries like healthcare, finance, and government are heavily scrutinized, requiring organizations to adhere to strict data protection and privacy regulations such as HIPAA, GDPR, PCI DSS, and SOX. These regulations often mandate the logging of security events and user activities. A standardized security daily activity log template helps ensure that your organization meets these requirements by providing a structured way to capture and store the necessary information, making audit preparations significantly smoother and less stressful.
Beyond compliance, these logs are invaluable for incident response and forensic analysis. When a security incident occurs, whether it’s a data breach or a system compromise, the first step is often to understand the scope and nature of the attack. Detailed activity logs provide the critical data points needed to reconstruct the timeline of events, identify the entry point, understand the attacker’s actions, and assess the damage. This rapid understanding is vital for containing the incident quickly and effectively, minimizing potential harm to your data and reputation.
Furthermore, consistent logging helps in identifying patterns and anomalies that might otherwise go unnoticed. Regular review of your security activity logs can reveal unusual login times, repeated failed access attempts from specific IP addresses, or unusual data transfers. These subtle indicators can be early warnings of a brewing security threat, allowing your team to take proactive measures before a minor issue escalates into a major crisis. It transforms reactive security into a predictive and preventative approach.
To truly be effective, a security daily activity log template needs to capture specific, actionable information. It’s not just about noting that something happened, but about providing enough detail to understand the context and impact. Without specific fields, the log can become vague and less useful when you really need it.
Key Elements to Include in Your Log
When designing or choosing your security daily activity log template, ensure it includes fields that prompt for thorough documentation. These elements are the backbone of a truly effective log, allowing for comprehensive data capture that aids in analysis, compliance, and incident response.
- Timestamp: The exact date and time of the activity.
- Description of Activity: A clear and concise summary of what occurred.
- User/Personnel Involved: The individual or system account that performed the action.
- System/Asset Affected: The specific server, application, network device, or data involved.
- Observed Outcome: Was the action successful, failed, or partially successful?
- Any Irregularities Noted: Any unusual observations, errors, or deviations from normal behavior.
- Reviewer/Auditor: The person who reviewed the log entry.
By including these specific categories, your template guides users to record the essential details, making each entry more valuable. Remember, the goal is to create a living document that serves as an accurate and complete record of your security landscape.
Practical Tips for Implementing and Maintaining Your Activity Log
Once you’ve settled on a robust security daily activity log template, the next step is its effective implementation and ongoing maintenance. The best template in the world is useless if it’s not consistently used or properly managed. Start by clearly defining who is responsible for logging specific activities. Whether it’s IT administrators for system events, help desk personnel for user requests, or security officers for physical access, clarity in roles prevents gaps and ensures accountability. Training is paramount here; everyone involved needs to understand the importance of the log, how to fill it out accurately, and what constitutes a reportable event.
Consistency is truly the secret ingredient. Make logging a regular, non-negotiable part of daily operations rather than an afterthought. This might involve setting daily reminders, integrating log entries into existing workflows, or even using automated tools where possible to populate certain fields. The less friction there is in the logging process, the more likely your team will adhere to it. Encourage detailed yet concise entries, avoiding jargon where plain language suffices, to ensure readability and understanding across different team members.
Secure storage and accessibility are another critical aspect. Your activity logs contain sensitive information about your security posture and operations. They must be stored in a manner that protects them from unauthorized access, modification, or deletion. Implement strict access controls, backup procedures, and retention policies. While secure, the logs also need to be readily accessible to authorized personnel for review, analysis, and auditing purposes. Consider using a centralized logging system or a secure cloud solution that offers both protection and ease of retrieval.
Finally, establish a regular review process. Simply collecting data isn isn’t enough; the insights come from analyzing it. Designate individuals or teams responsible for reviewing the logs on a daily, weekly, or monthly basis, depending on the volume and criticality of the information. This review should look for patterns, anomalies, potential threats, and areas for improvement in your security protocols. A structured review process ensures that the valuable data within your activity logs is actually leveraged to strengthen your overall security posture and adapt to evolving threats.
Embracing a systematic approach to security logging, spearheaded by a thoughtful security daily activity log template, is more than just a procedural task; it’s a strategic investment in your organization’s resilience. These logs transform nebulous events into tangible data, empowering your team to detect, respond to, and mitigate threats with greater precision and speed. By fostering a culture of meticulous documentation, you’re not just preparing for audits, but actively building a more secure and trustworthy environment for everyone involved.
Ultimately, the commitment to maintaining detailed activity records cultivates a proactive security mindset throughout your entire organization. It transitions your defense from a reactive scramble to an informed, continuous process of improvement and vigilance. This consistent effort, supported by clear templates and defined processes, ensures your security posture remains strong, adaptive, and prepared for whatever challenges the digital landscape may present.